Rear Area Security & Counter-Reconnaissance Battle
The Rear Area Lines of Communication (LOC) Battle is Back to Front.
Rear Area Security & Counter-Reconnaissance Battle
The Rear Area Lines of Communication (LOC) Battle is Back to Front.
Mission:
Our logistics and Lines of Communication / LOCs are compromised by enemy drones and the indirect fires they summon operating over the rear area. We must deny the enemy air/drone mobility over our rear areas to restore our own mobility in our LOCs (Lines of Communication) from the battalion-level CPs back.
This will be accomplished in three phases using swarming principles, beginning dispersed, then massing to apply force, then dispersing again—a pulsing tactic inherent to swarming.
Phase 1: Counter-Reconnaissance / Counter-Drone Operations
Objective: Deny enemy ISR access over rear areas—winning the counter-recon fight before any sustained logistics movement is possible. (ISR-Intelligence, Surveillance, Reconnaissance).
Concept of Operations
Regenerate from dispersed to mass against detected enemy ISR threats.
Rear-area security forces (logistics troops, MPs, ADA units, counter-drone units) start dispersed to minimize detection.
Upon detection of enemy ISR drones or ground reconnaissance, nearby units self-organize (regenerate) into ad hoc hunter-killer teams using available assets (short-range drones, counter-drone jammers, AAA, etc.).
After neutralization, forces immediately disperse again, avoiding predictable massing that could invite enemy strikes.
ISR Denial Through Pulsing Swarms
Rear-area forces launch short bursts of massed counter-drone activity, actively hunting enemy ISR, then quickly dissolve back into smaller, dispersed formations.
Think of it as electronic "ambushes" on enemy ISR—AI-driven drone swarms, jammers, and kinetic defenses activate, engage, and vanish before enemy fires can retaliate.
End State:
Enemy ISR is denied over rear areas, meaning logistics units can move without immediate detection and targeting.
We have air dominance (and ground control if applicable) over our LOCs.
Phase 2: Reestablishing Ground & Air Mobility in Rear Areas
Objective: Restore functional logistics corridors and protected supply routes.
Concept of Operations
Adopt a decentralized, dynamically adapting LOC system
No static supply depots: instead, we use micro-depots, mobile caches, and dispersed convoys that move only after Phase 1 success.
Regenerative convoys: Instead of single, large formations, logistics moves in dispersed elements that self-reassemble at key points before dispersing again after unloading. This is very similar to how networks deliver packets of data, indeed similar to our ‘packetized’ media culture and even conversation now, which means we’re already thinking this way. So DO the way we THINK or at least MOVE the way we really Communicate.
Layered Security on LOCs
Now that Phase 1 cleared enemy ISR, counter-recon forces escort logistics elements along reestablished supply routes.
"Rolling defense" model: A mix of mobile ADA, electronic warfare (EW) units, and counter-recon teams constantly shift along LOCs, preventing enemy infiltration.
End State:
We have secured primary and secondary logistics corridors, restoring supply movement without catastrophic losses.
Phase 3: Maintain Security & Mobility in Rear Areas
Objective: Sustain protected LOCs while adapting to emerging enemy threats.
Concept of Operations
Adaptability in Rear Security
Use automated AI-assisted reconnaissance to dynamically shift LOC security elements based on real-time threats.
Maintain continuous drone and counter-drone patrols to deny enemy infiltration with ISR assets.
Self-Healing Rear-Areas
If an enemy breakthrough occurs, we regenerate defenses from dispersed assets to quickly isolate and eliminate penetration.
Rear-area security pulses continue—massing to strike, then dispersing.
End State:
The rear area is stable enough to enable sustained combat operations, and maneuver forces can now shift focus forward instead of constantly fighting to sustain themselves.
Execution: Using Swarming Principles to Generate & Regenerate Rear Area Security
Regeneration: Rear-area forces begin dispersed and reassemble into temporary formations only when needed, preventing the enemy from tracking and targeting them.
Massing/Dispersal Pulses: Just like swarming, logistics and security forces only concentrate when there is an immediate advantage, then break apart before the enemy can react.
Dynamic Tasking: Forces self-organize based on local situational awareness, using secure channels to coordinate without a single vulnerable central node.
Summary: Fighting the War in Reverse
Instead of supporting the front, we start by securing the rear.
Only after rear area security is established can maneuver forces fully operate forward.
This flips traditional logistics planning on its head—but it’s the only way to survive in a battlefield of total ISR transparency.
Mission Contracts: mission orders in contract form. Herman Black of the WW2 German Army defined Auftragstaktik [Mission orders] as ‘contracts’ between the Superior and the Subordinate, what the Superior intends done and what the Subordinate needs from his Boss. Every American understands Contract and getting the job done. CONTRACT.
In the Spirit of Mission Command - Herein mission orders are reduced to Mission Contracts.
Tracking Mission Contracts Across Echelons in Rear Area / LOC battle.
Objective:
Ensure mission contracts (mission command via mission threads) are tracked seamlessly across different echelons, enabling rapid execution, clear responsibilities, decentralized action, and real-time adaptation.
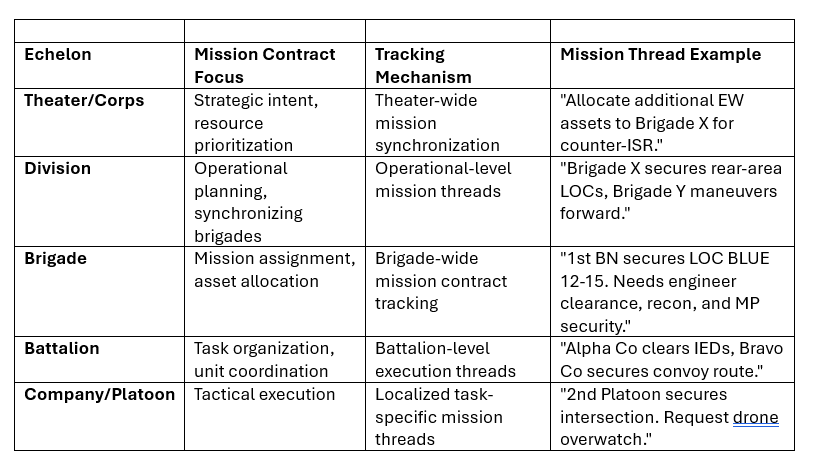
1. Mission Contracts Flowing Through Echelons
Each echelon tracks mission contracts within its own Virtual Channels while staying connected to both higher and lower levels for dynamic adjustments.
Virtual Channels are simply a digital channel established across ANY digital communications, Chat or Chat Room is a virtual channel. Any communication equipment will do this including your phone. Keep in mind security of transmission and emissions.
VIRTUAL CHANNELS
2. How Mission Contracts Are Tracked
A. Persistent Mission Threads for Execution & Updates
Mission contracts flow inside their designated Virtual Channel threads
Each mission thread remains active until completion, ensuring:
Live status tracking
Continuous updates across echelons
Real-time problem-solving
Example:
📡 "1st Battalion: Secure LOC BLUE 12-15"
🔄 Live Updates in Thread:
✅ Engineers beginning clearance
✅ Scout drones detect enemy ISR
✅ Counter-drone team engaging
✅ Convoy cleared to move
Once completed, the mission thread is archived but remains accessible for after-action review.
B. Dynamic Linking Between Echelons
Mission contracts at one echelon are directly linked to execution at the next level down.
Brigade issues a mission contract → Battalion executes it → Company refines tactical details.
Each echelon only focuses on what’s necessary at their level while maintaining visibility of the bigger picture.
💡 Commanders always see what they need—no unnecessary information overload.
C. Adaptive Mission Contracts: Adjusting in Real-Time
If battlefield conditions change, the mission contract updates dynamically in its thread.
Subordinates report status changes up, while higher command adjusts asset allocations down.
Echelons adapt without waiting for lengthy approval chains.
Example:
Brigade: "1st BN, adjust to securing LOC RED 7-9 instead. Engineer assets en route."
1st BN: "Acknowledged. Will re-task MP security to new corridor. ETA 30 mins."
Platoon Level: "Encountered resistance at checkpoint. Requesting fire support."
Brigade: "Fires allocated. Clear by fires then proceed."
This flow ensures decisions happen instantly, eliminating bureaucratic drag.
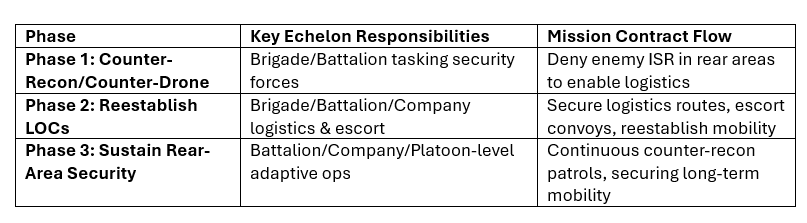
3. Mission Contract Execution by Phase
Mission contracts flow through echelons in sync with each operational phase:
Phase
Key Echelon Responsibilities
Mission Contract Flow
Phase 1: Counter-Recon/Counter-Drone
Brigade/Battalion tasking security forces
Deny enemy ISR in rear areas to enable logistics
Phase 2: Reestablish LOCs
Brigade/Battalion/Company logistics & escort
Secure logistics routes, escort convoys, reestablish mobility
Phase 3: Sustain Rear-Area Security
Battalion/Company/Platoon-level adaptive ops
Continuous counter-recon patrols, securing long-term mobility
Each phase is tracked in Virtual Channels, ensuring mission contracts evolve in real time without disrupting execution.
MISSION CONTRACTS FLOW BY PHASE
4. Summary: How Mission Contracts Are Tracked
✅ Each echelon operates inside its own Virtual Channels, linked up and down the chain.
✅ Mission contracts flow inside persistent mission threads, ensuring clarity and accountability.
✅ Subordinates execute without micromanagement; mission contracts update dynamically based on conditions.
✅ Mission contracts follow a structured phase-based approach, ensuring seamless operational flow.


dropping knowledge per usual.
Wouldn't it be easier (and cheaper!) just to get along?
I know, I know... Just saying.